Behind the Code: Why Your Business Can't Afford to Overlook Basic Cyber Defense
...but security can’t be an afterthought
As a nation, we’re beginning to appreciate the value of technology. Our businesses are slowly realizing the advantages of embracing and leveraging what it has to offer. Today, it’s almost impossible to find a business that doesn’t rely on websites, CRMs, mobile apps, bots, and other digital tools. While these technologies enhance our business operations, drive sales, and improve customer engagement, they also introduce significant security risks—risks that can compromise both customer data and organizational integrity.
In this article, we’ll dive into one of these risks, unpack it, and discuss why it’s crucial for businesses to invest in robust cybersecurity measures. I know, sometimes we prioritize speed and agility, rushing to deploy new features in order to beat competitors to market. But security can’t be an afterthought.
Enough of the intro—let's dive in!
One day, while scrolling through my Twitter feed, I came across a post encouraging people to vote for our local artist, JP, and other Zimbabwean artists. Naturally, I followed the link, cast my vote for JP and a few other favorites, and felt satisfied. But then a thought crossed my mind: What if I could automate this? Imagine building a bot that could cast votes on my behalf—sounds cool, right? So, I started exploring the site, gathering information, and formulating a plan.
The Key Question: What Security Measures Are in Place?
1. Google reCaptcha:
The site uses Google reCaptcha, which is one of the most common defenses against automated bots. It's a solid security measure, but its effectiveness largely depends on how it's implemented. The real problem with reCaptcha is the possibility of CAPTCHA bypass if it’s not configured properly. For example, many developers use a simple threshold, like checking if the reCaptcha score is above a certain value (e.g., 0.7 or 7/10). But here's the question: Can our bot mimic a legitimate user well enough to pass the reCaptcha verification?
The answer is yes—if we can simulate user interaction, like moving the cursor around, typing, or even clicking in random places. With a few lines of Python code, this becomes a trivial task. By using a bot that mimics human behavior, it’s possible to achieve a high reCaptcha score, even though the interaction is completely automated. This is why relying solely on reCaptcha for bot mitigation is insufficient—it must be paired with additional layers of defense.
{ "event":{ "expectedAction":"EXPECTED_ACTION", "hashedAccountId":"ACCOUNT_ID", "siteKey":"KEY_ID", "token":"TOKEN", "userAgent":"(USER-PROVIDED STRING)", "userIpAddress":"USER_PROVIDED_IP_ADDRESS" }, "name":"ASSESSMENT_ID", "riskAnalysis":{
"reasons":[],
"score":"SCORE"
},
"tokenProperties":{ "action":"USER_INTERACTION", "createTime":"TIMESTAMP", "hostname":"HOSTNAME", "invalidReason":"(ENUM)", "valid":(BOOLEAN) } }2. Input Sanitization:
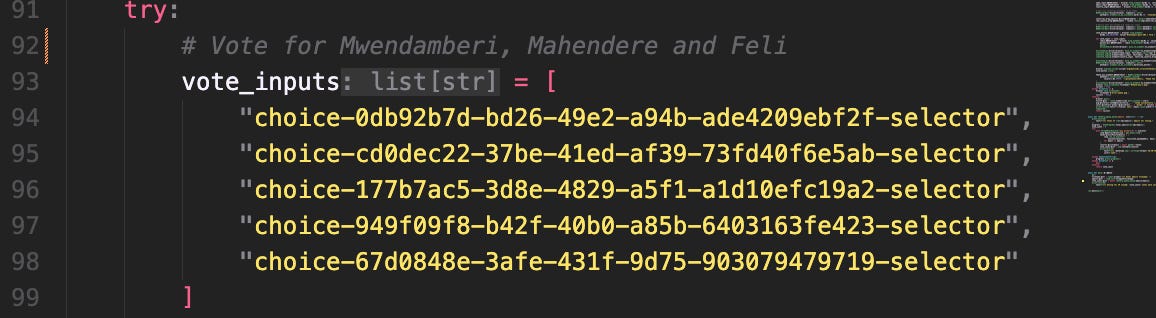
Another critical area is input validation. Does the site sanitize the inputs properly, or can I submit arbitrary values without triggering a vulnerability? In this case, the site does sanitize inputs, but here's a flaw: it doesn’t check for email uniqueness. That means you can technically vote multiple times using same email address. This was particularly useful for my bot, which leveraged both real and dummy email addresses.
For this bot, I scraped about 6,000 email addresses—plenty of them were valid but others were fake. This brings up an important point: even if your site sanitizes input, it must also validate data on the backend (e.g., checking for duplicate email submissions or flagging suspicious patterns of activity).
3. IP Address Detection:
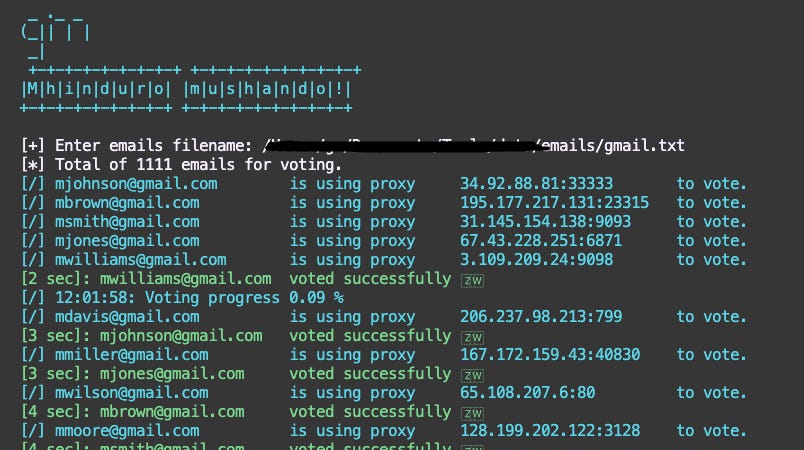
Next, I wondered if the site collects and monitors IP addresses to prevent multiple votes from the same user. While it’s not clear if they’re tracking IPs, there’s always a risk that my votes could get rejected if multiple submissions come from the same IP address. The solution? Proxies and VPNs. By using proxy rotation, I could hide the bot’s actual location, making each request appear to come from a different IP.
However, there’s a catch: a well-designed site can detect and block proxy traffic through techniques like IP fingerprinting or IP geolocation analysis. Additionally, if the site employs rate limiting or behavioral analytics, even proxy-based strategies could fail if they spot unusual traffic patterns or suspicious activity, such as too many requests in a short period.
The Bot in Action: vote_jp.py
Armed with all this knowledge, I wrote a Python script called vote_jp.py. It wasn’t long before the bot started casting votes—over 10,000 votes across 5 categories, with 3 of them winning. Sure, real people cast votes too, but the bot definitely contributed significantly to the outcome.
While bots can seem harmless, they’re actually highly disruptive and pose a real threat to the integrity of online systems. In this case, I was able to manipulate the voting system, but the impact on businesses can be far worse. Bots can skew results, steal sensitive data, or even launch Distributed Denial-of-Service (DDoS) attacks that overwhelm a website and disrupt business operations.
Why Cybersecurity Investment is Essential
As demonstrated, bots can undermine trust and cause severe damage, especially if there are vulnerabilities in your system. That’s why businesses need to think beyond just deploying technology—they must adopt a defense-in-depth strategy that includes robust bot mitigation, input validation, real-time traffic monitoring, and multi-layered authentication systems.
Cybersecurity is a constantly evolving field, and threats like these are becoming more sophisticated. You can’t afford to let your guard down, especially when automated bots are becoming increasingly advanced in their ability to evade detection.
So what’s the takeaway here? Always invest in cybersecurity from the ground up. Hire professionals who understand the nuances of secure application development, who can implement advanced techniques like rate limiting, two-factor authentication (2FA), and machine learning-based anomaly detection to safeguard your digital assets. Security should be an integral part of your business strategy—not an afterthought.


Welcome to substack, Gift.